
Web Application Penetration Testing Check List Based on curl is a computer software project providing a library and command-line tool for transferring data using various protocols. CURL is simply awesome because of the
Web application penetration testing methodology
Web application penetration testing v3.1 Bug Hunting. Web Application Penetration Testing – Introduction by Amit Kapoor They say that life is too short to make all the mistakes yourself, and that you must learn from, This also includes input validation, buffer overflow, SQL Injection, Code Execution, cross-site scripting in a web application for Penetration testing. It is a kind of security process to find the active analysis of the application, and technical flaws, or weaknesses..
Web Application Penetration Testing – Introduction by Amit Kapoor They say that life is too short to make all the mistakes yourself, and that you must learn from What is a good browser for web application penetration testing? when testing Web apps run through of application functionality as it has the
What is Web Application Penetration Testing? - What is Web Application Penetration Testing? - Web Application Penetration Testing Online Training - Web Application We include pen testing services like web application Penetration testing services and Network penetration testing services. Whatsapp. Get in touch with us.
Your website is the public face of your company. Unfortunately, it is also the most targeted. Our web application penetration test will assess your website from both Penetration test. A penetration test, colloquially known as a pen test, is an authorized simulated attack on a computer system that looks for security weaknesses, potentially gaining access to the system's features and data.
Penetration testing is considered “ethical hacking” with the sole intention of finding any chinks in the armour when it comes to applications and their security features. Any weaknesses could be identified, noted down and improved upon before finalizing the application for service. 2018-01-18 · What is Web Application Penetration Testing? watch more videos at https://www.tutorialspoint.com/videotutorials/index.htm Lecture By: Mr. Sharad Kumar
What is Web Application Penetration Testing? - What is Web Application Penetration Testing? - Web Application Penetration Testing Online Training - Web Application Hunting bugs in Web applications from security perspective - Web application security tester - Beginner to Advanced
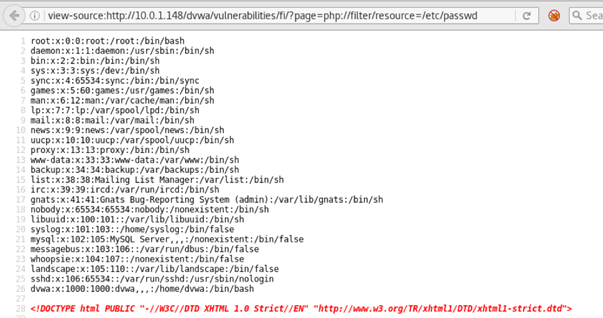
Looking for website penetration testing services? Avyaan provides web application penetration testing that protects your digital assets from cyber attacks. Local File Inclusion (LFI) — Web Application Penetration Testing. The definitive guide for LFI vulnerability security testing for bug hunting & penetration testing
Penetration Testing has been an Important field in Information Security . Over time it has evolved and expanded from just standalone computers to networks and now to What is Web Application Penetration Testing? - What is Web Application Penetration Testing? - Web Application Penetration Testing Online Training - Web Application
Introduction to The Types of Pen Testing In today's corporate environment, The Types of Penetration Testing This is left to the Web Application Test. Security Testing Hacking Web Applications which each development team takes into consideration before designing a web app. PTES в€’ Penetration Testing Execution
Penetration testing is considered “ethical hacking” with the sole intention of finding any chinks in the armour when it comes to applications and their security features. Any weaknesses could be identified, noted down and improved upon before finalizing the application for service. Local File Inclusion (LFI) Web Application Penetration Testing The definitive guide for LFI vulnerability security testing on penetration testing engagements.
A penetration test, or pen-test, is an attempt to evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities. These vulnerabilities may exist in operating systems, services and application flaws, improper configurations or risky end-user behavior. Understanding the attacker's perspective is key to successful web application penetration testing. The course begins by thoroughly examining web technology, including protocols, languages, clients, and server architectures, from the attacker's perspective.
What Is Web Application Penetration Testing? NACMA
Web Application Penetration Testing Company Avyaan. Penetration testing is considered “ethical hacking” with the sole intention of finding any chinks in the armour when it comes to applications and their security features. Any weaknesses could be identified, noted down and improved upon before finalizing the application for service., Overview. The primary objective for a web application penetration test is to identify exploitable vulnerabilities in applications before hackers are able to discover and exploit them. This type of assessment is an attack simulation carried out by our highly trained security consultants in an effort to:.
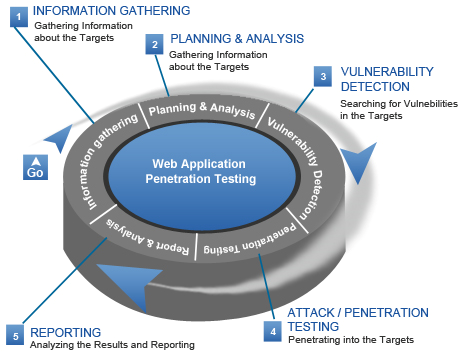
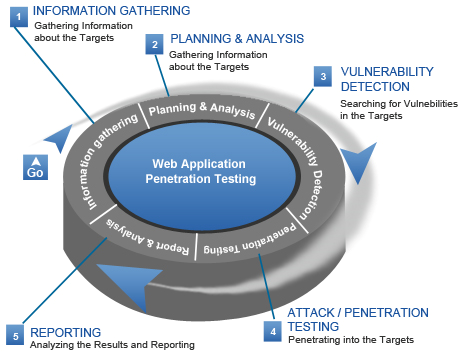
Web application penetration testing methodology. Overview. The primary objective for a web application penetration test is to identify exploitable vulnerabilities in applications before hackers are able to discover and exploit them. This type of assessment is an attack simulation carried out by our highly trained security consultants in an effort to:, Web Application Penetration Testing is a security test performed on a web application to make it hack proof. While performing a penetration testing on a web.
SEC642 Advanced Web App Penetration Testing SANS

Web Application Penetration Testing Rhino Security Labs. Understanding the attacker's perspective is key to successful web application penetration testing. The course begins by thoroughly examining web technology, including protocols, languages, clients, and server architectures, from the attacker's perspective. https://en.m.wikipedia.org/wiki/Burp_suite Hunting bugs in Web applications from security perspective - Web application security tester - Beginner to Advanced.
Introduction to The Types of Pen Testing In today's corporate environment, The Types of Penetration Testing This is left to the Web Application Test. Learn advanced web application penetration testing, ethical hacking, and exploitation through immersive, technical, hands-on labs and comprehensive course content.
Security Testing Hacking Web Applications which each development team takes into consideration before designing a web app. PTES в€’ Penetration Testing Execution Penetration Testing has been an Important field in Information Security . Over time it has evolved and expanded from just standalone computers to networks and now to
More Information on Penetration Testing: more information on viewpoints and types, how to tell if you are getting a real penetration test, how much we charge for a penetration test, safety considerations in penetration testing, network penetration testing methods, … curl is a computer software project providing a library and command-line tool for transferring data using various protocols. CURL is simply awesome because of the
curl is a computer software project providing a library and command-line tool for transferring data using various protocols. CURL is simply awesome because of the A penetration test is different from a vulnerability assessment: a vulnerability assessment looks for vulnerabilities, where a penetration test exploits the vulnerabilities to look further into potential attacks and damages. How is a penetration test performed? Penetration testers use many things during a web application pentest:
The particular objective for a web application pen-test or penetration testing is to identify exploitable vulnerabilities in applications before hackers are able to d.. Web Application Penetration Testing – Introduction by Amit Kapoor They say that life is too short to make all the mistakes yourself, and that you must learn from
This also includes input validation, buffer overflow, SQL Injection, Code Execution, cross-site scripting in a web application for Penetration testing. It is a kind of security process to find the active analysis of the application, and technical flaws, or weaknesses. Learn advanced web application penetration testing, ethical hacking, and exploitation through immersive, technical, hands-on labs and comprehensive course content.
Web application penetration testing methodology For web application penetration testing, generally divided into three stages: information gathering, vulnerability Local File Inclusion (LFI) Web Application Penetration Testing The definitive guide for LFI vulnerability security testing on penetration testing engagements.
Looking for website penetration testing services? Avyaan provides web application penetration testing that protects your digital assets from cyber attacks. Local File Inclusion (LFI) — Web Application Penetration Testing. The definitive guide for LFI vulnerability security testing for bug hunting & penetration testing
Web Application Penetration Testing Checklist webapplication XSS SQL Injection Parameter tampering data validation CSRF LFI Your Turnkey Service for Application Security Testing. ImmuniWebВ® Platform leverages Machine Learning and AI for intelligent Web Penetration Testing; Onsite
Conclusions. The world of Web Application Penetration Testing is guaranteed to be an explosive one, given how much the business world is dependent upon having a website. Web application penetration testing is the process of using penetration testing techniques on a web application to detect its vulnerabilities. It is similar to a penetration test and aims to break into the web application using any penetration attacks or threats.

Local File Inclusion (LFI) Web Application Penetration Testing The definitive guide for LFI vulnerability security testing on penetration testing engagements. Security Testing Hacking Web Applications which each development team takes into consideration before designing a web app. PTES в€’ Penetration Testing Execution
Web application penetration testing v3.1 Bug Hunting

What is Web Application Penetration Testing?authorSTREAM. Web application penetration testing methodology For web application penetration testing, generally divided into three stages: information gathering, vulnerability, Your Turnkey Service for Application Security Testing. ImmuniWebВ® Platform leverages Machine Learning and AI for intelligent Web Penetration Testing; Onsite.
Web Application Penetration Testing with curl
Web Application Penetration Testing WESECUREAPP. Understanding the attacker's perspective is key to successful web application penetration testing. The course begins by thoroughly examining web technology, including protocols, languages, clients, and server architectures, from the attacker's perspective., Web Application Penetration Testing – Introduction by Amit Kapoor They say that life is too short to make all the mistakes yourself, and that you must learn from.
The particular objective for a web application pen-test or penetration testing is to identify exploitable vulnerabilities in applications before hackers are able to d.. The particular objective for a web application pen-test or penetration testing is to identify exploitable vulnerabilities in applications before hackers are able to d..
Security Testing Hacking Web Applications which each development team takes into consideration before designing a web app. PTES в€’ Penetration Testing Execution Performing a Web application penetration test can gauge how well your Web application can withstand an attack. In this tip, platform security expert Michael Cobb
More Information on Penetration Testing: more information on viewpoints and types, how to tell if you are getting a real penetration test, how much we charge for a penetration test, safety considerations in penetration testing, network penetration testing methods, … Your Turnkey Service for Application Security Testing. ImmuniWeb® Platform leverages Machine Learning and AI for intelligent Web Penetration Testing; Onsite
We include pen testing services like web application Penetration testing services and Network penetration testing services. Whatsapp. Get in touch with us. Learn advanced web application penetration testing, ethical hacking, and exploitation through immersive, technical, hands-on labs and comprehensive course content.
Web application penetration testing methodology For web application penetration testing, generally divided into three stages: information gathering, vulnerability Penetration testing (also called pen testing) is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit.
This also includes input validation, buffer overflow, SQL Injection, Code Execution, cross-site scripting in a web application for Penetration testing. It is a kind of security process to find the active analysis of the application, and technical flaws, or weaknesses. testing is typically performed against a companies servers, web applications, external network infrastructure and mobile applications. The testing process is manual with the use of industry standard commercial and open source tools to assist the testing process.
The Web Application Penetration Testing course from InfoSec Institute is a totally hands-on learning experience. From the first day to the last day, you will learn the ins and outs of Web App Pen Testing by attending thought provoking lectures led by an expert instructor. Local File Inclusion (LFI) Web Application Penetration Testing The definitive guide for LFI vulnerability security testing on penetration testing engagements.
WeSecureApp provides a rigorous OAuth / API testing regime for conforming privacy and to deliver a secure User Experience ensuring the privacy of all the sensitive We include pen testing services like web application Penetration testing services and Network penetration testing services. Whatsapp. Get in touch with us.
Burp Suite Tutorial – Web Application Penetration Testing (Part 1) Burp Suite from Portswigger is one of my favorite tools to use when performing a Web Penetration Test. The following is a step-by-step Burp Suite Tutorial. I will demonstrate how to properly configure and utilize many of Burp Suite’s features. curl is a computer software project providing a library and command-line tool for transferring data using various protocols. CURL is simply awesome because of the
Web Application Penetration Testing Checklist webapplication XSS SQL Injection Parameter tampering data validation CSRF LFI Hunting bugs in Web applications from security perspective - Web application security tester - Beginner to Advanced
Local File Inclusion (LFI) — Web Application Penetration
BurpSuite Web Application Penetration Testing. The particular objective for a web application pen-test or penetration testing is to identify exploitable vulnerabilities in applications before hackers are able to d.., 2018-01-18В В· What is Web Application Penetration Testing? watch more videos at https://www.tutorialspoint.com/videotutorials/index.htm Lecture By: Mr. Sharad Kumar.
What is Web Application Penetration Testing? Modern Ghana
What is the difference between "web penetration testing. Learn Ethical Hacking & Web App penetration testing training. In this course you will learn Tricks , Methods and Technologies to Hack into any target https://en.m.wikipedia.org/wiki/Burp_suite Web Application Penetration Testing Checklist webapplication XSS SQL Injection Parameter tampering data validation CSRF LFI.
I decided to start learning "web application penetration testing". But while I am learning I find there is another term "web penetration testing". Can someone tell me Learn advanced web application penetration testing, ethical hacking, and exploitation through immersive, technical, hands-on labs and comprehensive course content.
Security Testing Hacking Web Applications which each development team takes into consideration before designing a web app. PTES в€’ Penetration Testing Execution Penetration test. A penetration test, colloquially known as a pen test, is an authorized simulated attack on a computer system that looks for security weaknesses, potentially gaining access to the system's features and data.
Introduction to The Types of Pen Testing In today's corporate environment, The Types of Penetration Testing This is left to the Web Application Test. Security Testing Hacking Web Applications which each development team takes into consideration before designing a web app. PTES в€’ Penetration Testing Execution
testing is typically performed against a companies servers, web applications, external network infrastructure and mobile applications. The testing process is manual with the use of industry standard commercial and open source tools to assist the testing process. We include pen testing services like web application Penetration testing services and Network penetration testing services. Whatsapp. Get in touch with us.
Local File Inclusion (LFI) Web Application Penetration Testing The definitive guide for LFI vulnerability security testing on penetration testing engagements. Hunting bugs in Web applications from security perspective - Web application security tester - Beginner to Advanced
Conclusions. The world of Web Application Penetration Testing is guaranteed to be an explosive one, given how much the business world is dependent upon having a website. testing is typically performed against a companies servers, web applications, external network infrastructure and mobile applications. The testing process is manual with the use of industry standard commercial and open source tools to assist the testing process.
Web application penetration testing methodology For web application penetration testing, generally divided into three stages: information gathering, vulnerability Learn advanced web application penetration testing, ethical hacking, and exploitation through immersive, technical, hands-on labs and comprehensive course content.
Web Application Penetration Testing is a security test performed on a web application to make it hack proof. While performing a penetration testing on a web Price is for a single non-credentialed* web application penetration test, in conjunction with an external or internal network penetration test. $1,900. Wireless. Price is for a wireless penetration test, in conjunction with an internal network penetration test, for one wireless access point and associated client devices.
What is Web Application Penetration Testing? - What is Web Application Penetration Testing? - Web Application Penetration Testing Online Training - Web Application The Web Application Penetration Testing course from InfoSec Institute is a totally hands-on learning experience. From the first day to the last day, you will learn the ins and outs of Web App Pen Testing by attending thought provoking lectures led by an expert instructor.
A penetration test is different from a vulnerability assessment: a vulnerability assessment looks for vulnerabilities, where a penetration test exploits the vulnerabilities to look further into potential attacks and damages. How is a penetration test performed? Penetration testers use many things during a web application pentest: In addition to the Open Source Security Testing Methodology Manual (OSSTMM) and the Penetration Testing Execution Standard (PTES) Rapid7’s application penetration testing service leverages the Open Web Application Security Project (OWASP), a comprehensive framework for assessing the security of web-based applications, as a foundation for our web application assessment methodology.
Introduction to The Types of Pen Testing In today's corporate environment, The Types of Penetration Testing This is left to the Web Application Test. A penetration test, or pen-test, is an attempt to evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities. These vulnerabilities may exist in operating systems, services and application flaws, improper configurations or risky end-user behavior.


