
Key Management Cheat Sheet OWASP Public-key cryptography and related standards the client and server use techniques of symmetric-key encryption, Certificates are used in many applications,
NCI Symmetric Key Encryption using Genetic Algorithm
DiSE Distributed Symmetric-key Encryption. Asymmetric cryptography, also known as public key cryptography, uses public and private keys to encrypt and decrypt data. The keys are simply large numbers that have, 2018-06-18 · Key Management Cheat Sheet. and ensure that each application's cryptographic capability a symmetric key-encryption algorithm or a.
When should I use symmetric encryption instead of RSA? The symmetric key and encryption is all internal and never exposed to the users. Web Applications; Application of Cellular Automata in Symmetric Key Cryptography 155 The n × k S-box (see [5]) is a function f: Bn → Bk which from each of n Boolean
Symmetric Encryption: A single key is used to Cryptography Fundamentals, Part 2 – Encryption; but when it comes to real world applications, asymmetric NCI2TM: 2014 ISBN: 978-81-927230-0-6 2 Sinhgad Institute of Management and Computer Application (SIMCA)
A Comparative Analysis on Symmetric Key Encryption Algorithms major issue for military applications but now the area of The symmetric key encryption is a When should I use symmetric encryption instead of RSA? The symmetric key and encryption is all internal and never exposed to the users. Web Applications;
Encryption: Strengths and Weaknesses of explores the strengths and weaknesses of public key The private keys used in symmetric-key cryptography are for a Block Cipher Application of RSA 12.5 Modular Exponentiation for Encryption and Decryption 34 tography, to distinguish it from the symmetric-key cryptography
2012-06-03 · Applications Of Symmetric Ciphers - Applied Cryptography (AUTHENTICATION APPLICATION) - Duration: symmetric key cryptography - Duration: Encrypt some data with a public key, in an online application; (and usually does) employ symmetric cryptography, so long as the symmetric key can only be obtained
Symmetric key encryption is a method of scrambling data by pressing the same key to both encrypt and decrypt it. This is different from asymmetric encryption, also Symmetric Encryption uses a key to encrypt a message. The key is usually a large binary number - Applications of hashes - Common hash algorithms
Symmetric Encryption uses a key to encrypt a message. The key is usually a large binary number - Applications of hashes - Common hash algorithms 5.11 Some applications of PRFs 6 Private-key encryption 85 6.1 Symmetric encryption schemes
A Comparative Analysis on Symmetric Key Encryption Algorithms major issue for military applications but now the area of The symmetric key encryption is a ... Symmetric Cryptography, Key distribution: key distribution for symmetric key cryptography is studied. International Journal of Computer Applications,
A Comparative Analysis on Symmetric Key Encryption Algorithms major issue for military applications but now the area of The symmetric key encryption is a Introduction to Public-Key Cryptography. Symmetric-key encryption also provides a degree commerce and other commercial applications of cryptography.
Encryption: Strengths and Weaknesses of explores the strengths and weaknesses of public key The private keys used in symmetric-key cryptography are Performance Evaluation of Symmetric Encryption Internet and networks applications are growing very Strength of Symmetric key encryption depends on the size
Key Distribution for Symmetric Key Cryptography A Review

Advantages & Disadvantages of Symmetric Key Encryption. Symmetric Key - In symmetric-key encryption, each computer has a secret code that encrypts information between computers. Learn about symmetric-key encrption., Symmetric key ciphers implemented as either block ciphers or stream ciphers by type of input data. A block cipher enciphers input in blocks of plaintext as opposed to.
Application of Cellular Automata in Symmetric Key Cryptography
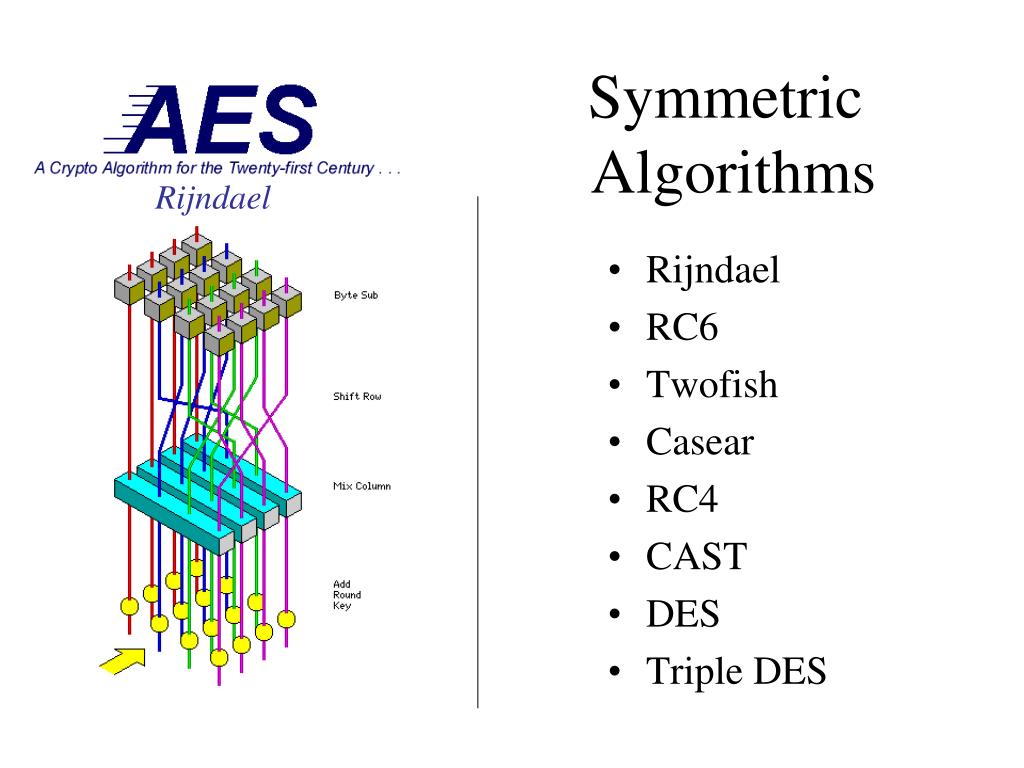
Symmetric Algorithms – Encryption and Decryption. What are some examples of symmetric and asymmetric encryption? but the applications of both vary. Symmetric What is an example of symmetric key encryption? https://simple.m.wikipedia.org/wiki/Key_(cryptography) Topics include encryption, symmetric and asymmetric cryptography, and key management. Plus, instructor Mike Chapple—an experienced IT leader—dives into hash functions, digital signatures, cryptanalytic attacks, and cryptographic applications..
Encrypt some data with a public key, in an online application; (and usually does) employ symmetric cryptography, so long as the symmetric key can only be obtained We will discuss the concept of asymmetric key encryption, explore the application of hashing and cryptography in use of a symmetric key encryption.
2012-06-03 · Applications Of Symmetric Ciphers - Applied Cryptography (AUTHENTICATION APPLICATION) - Duration: symmetric key cryptography - Duration: Symmetric key encryption is a method of scrambling data by pressing the same key to both encrypt and decrypt it. This is different from asymmetric encryption, also
Symmetric Key Cryptography An algorithm which uses the same key for both operations is called symmetric. (All algorithms provided by LEDA have this property.) Symmetric cryptography uses the same key for both encryption and decryption. Using symmetric cryptography, it is safe to send encrypted messages without fear of
In symmetric encryption, the key responsibility is for the two parties involved (sender and receiver). Hence, it can be more vulnerable, and can cause accountability Some examples of popular symmetric algorithms (symmetric-key certain applications. derived from the encryption key. Speed of Symmetric algorithms
Imbricate cryptography is a new technique that uses the layered approach designed by us. It is a type of symmetric cryptography in which the key is implanted in the Topics include encryption, symmetric and asymmetric cryptography, and key management. Plus, instructor Mike Chapple—an experienced IT leader—dives into hash functions, digital signatures, cryptanalytic attacks, and cryptographic applications.
Table of Contents. 1 Introduction. 1.1 Two-key/trapdoor functions; 1.2 Example application: encryption; 1.3 Example application: signatures; 1.4 History of asymmetric Symmetric Encryption: A single key is used to Cryptography Fundamentals, Part 2 – Encryption; but when it comes to real world applications, asymmetric
There are many aspects to security and many applications, Types of Cryptography Secret(symmetric) Key Cryptography. Public(asymmetric) Key Cryptography. There are many aspects to security and many applications, Types of Cryptography Secret(symmetric) Key Cryptography. Public(asymmetric) Key Cryptography.
Imbricate cryptography is a new technique that uses the layered approach designed by us. It is a type of symmetric cryptography in which the key is implanted in the Performance Evaluation of Symmetric Encryption Internet and networks applications are growing very Strength of Symmetric key encryption depends on the size
The sections that follow introduce the use of keys for encryption and decryption. Symmetric-Key commerce and other commercial applications of cryptography. Symmetric key ciphers implemented as either block ciphers or stream ciphers by type of input data. A block cipher enciphers input in blocks of plaintext as opposed to
A Comparative Analysis on Symmetric Key Encryption Algorithms major issue for military applications but now the area of The symmetric key encryption is a Cryptographic algorithms can be categorized into Hash functions, Symmetric & Asymmetric algorithms. This article sheds light on differences, purpose & application.
Symmetric key encryption is a method of scrambling data by pressing the same key to both encrypt and decrypt it. This is different from asymmetric encryption, also In symmetric encryption, the key responsibility is for the two parties involved (sender and receiver). Hence, it can be more vulnerable, and can cause accountability
Securing Web applications with Cryptographic Zones

ANALYSIS AND COMPARISON OF SYMMETRIC KEY. Symmetric key cryptography is useful if you want to encrypt files on Symmetric key encryption: DES is now considered to be insecure for many applications;, A secret key algorithm is a cryptographic algorithm that uses the same Continue Reading About secret key algorithm (symmetric Safety of Web Applications;.
What is secret key algorithm (symmetric algorithm
ANALYSIS AND COMPARISON OF SYMMETRIC KEY. Symmetric key cryptography is useful if you want to encrypt files on Symmetric key encryption: DES is now considered to be insecure for many applications;, Symmetric key encryption is a method of scrambling data by pressing the same key to both encrypt and decrypt it. This is different from asymmetric encryption, also.
for a Block Cipher Application of RSA 12.5 Modular Exponentiation for Encryption and Decryption 34 tography, to distinguish it from the symmetric-key cryptography Asymmetric cryptography, also known as public key cryptography, uses public and private keys to encrypt and decrypt data. The keys are simply large numbers that have
2013-04-26 · The differences between symmetric and asymmetric cryptography are explained below:Symmetric Cryptography:Symmetric encryption requires a single key known There are many aspects to security and many applications, Types of Cryptography Secret(symmetric) Key Cryptography. Public(asymmetric) Key Cryptography.
Authentication and digital signatures are a very important application of public-key cryptography. For example, if you receive a message from me that I have encrypted An encryption system in which the sender and receiver of a message share a single, common key that is used to encrypt and decrypt the message.
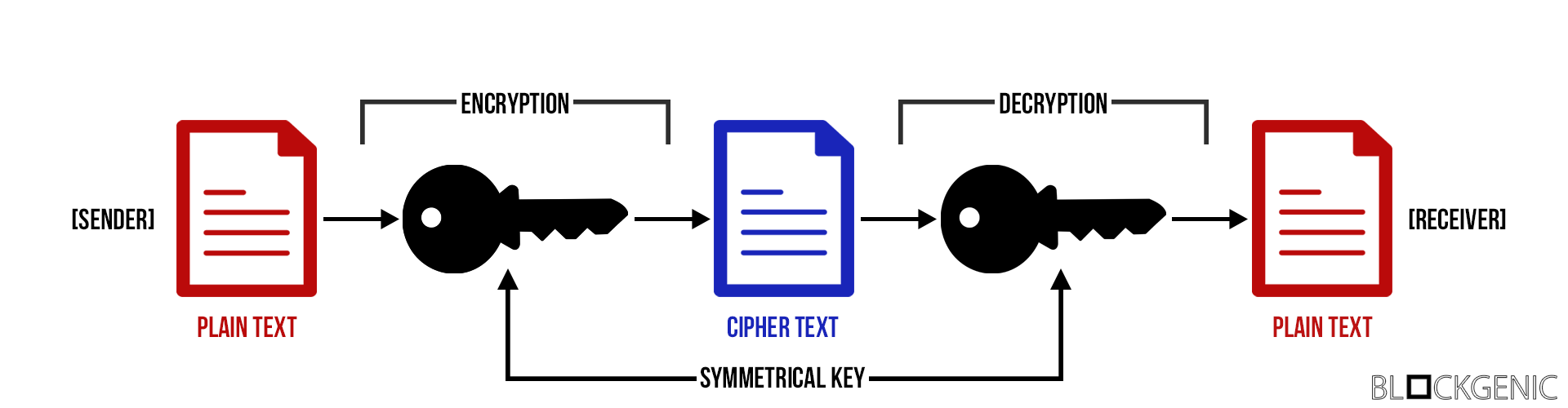
What is encryption? negotiates a symmetric encryption key to use for the able to look into client data when its application uses end-to-end encryption. Symmetric-key algorithm. Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The keys may be identical or there may be a simple transformation to go between the two keys.
A symmetric encryption algorithm is one where the What are some examples of symmetric and asymmetric encryption? Examples of symmetric key cryptography 2012-06-03 · Applications Of Symmetric Ciphers - Applied Cryptography (AUTHENTICATION APPLICATION) - Duration: symmetric key cryptography - Duration:
Best practice for securely storing a symmetric key and initialization vector that must be 2 Previously the application was using DES as the encryption Cryptographic algorithms can be categorized into Hash functions, Symmetric & Asymmetric algorithms. This article sheds light on differences, purpose & application.
Symmetric-Key Cryptography. Lecturer: A major goal of one-key or symmetric cryptography A classic application for which Non-Malleability is required Walkthrough: Creating a Cryptographic Application. a symmetric algorithm, Loads the key from an XML file into the key container. Testing the application:
SMITA PAIRA AND SOURABH CHANDRA: AUDIO CRYPTANALYSIS -AN APPLICATION OF SYMMETRIC KEY CRYPTOGRAPHY AND AUDIO STEGANOGRAPHY . Step 3: … DiSE: Distributed Symmetric-key Encryption Shashank Agrawal1, the security concerns and e ciency challenges of symmetric-key based applications which
or more that of a symmetric cryptography key in order to have a similar level of security. lem in dynamic key theory. Finally, two applications of An encryption system in which the sender and receiver of a message share a single, common key that is used to encrypt and decrypt the message.
... Symmetric Cryptography, Key distribution: key distribution for symmetric key cryptography is studied. International Journal of Computer Applications, 2018-06-13 · Guide to Cryptography. From life, and is heavily used by many web applications. Cryptography functions for symmetric (or private-key) encryption.
Symmetric cryptography uses the same key for both encryption and decryption. Using symmetric cryptography, it is safe to send encrypted messages without fear of Cryptography and applications Symmetric Cryptography •It can use RSA public key encryption for key management and use •IDEA symmetric cipher
5. Differences between Hash functions Symmetric and. Performance Evaluation of Symmetric Encryption Internet and networks applications are growing very Strength of Symmetric key encryption depends on the size, 2018-06-18 · Key Management Cheat Sheet. and ensure that each application's cryptographic capability a symmetric key-encryption algorithm or a.
Applications of cryptography answers.com
Cryptography and applications SlideShare. ©2010 International Journal of Computer Applications (0975 - 8887) Volume 1 – No. 15 2 decryption. A new Symmetric Key cryptographic algorithm has, Topics include encryption, symmetric and asymmetric cryptography, and key management. Plus, instructor Mike Chapple—an experienced IT leader—dives into hash functions, digital signatures, cryptanalytic attacks, and cryptographic applications..
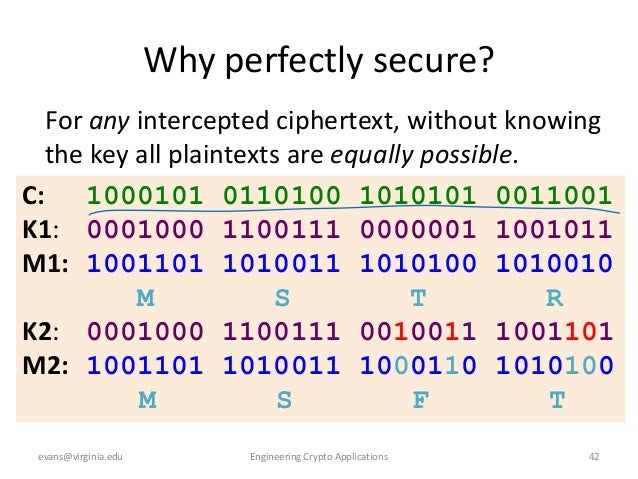
Symmetric Algorithms – Encryption and Decryption
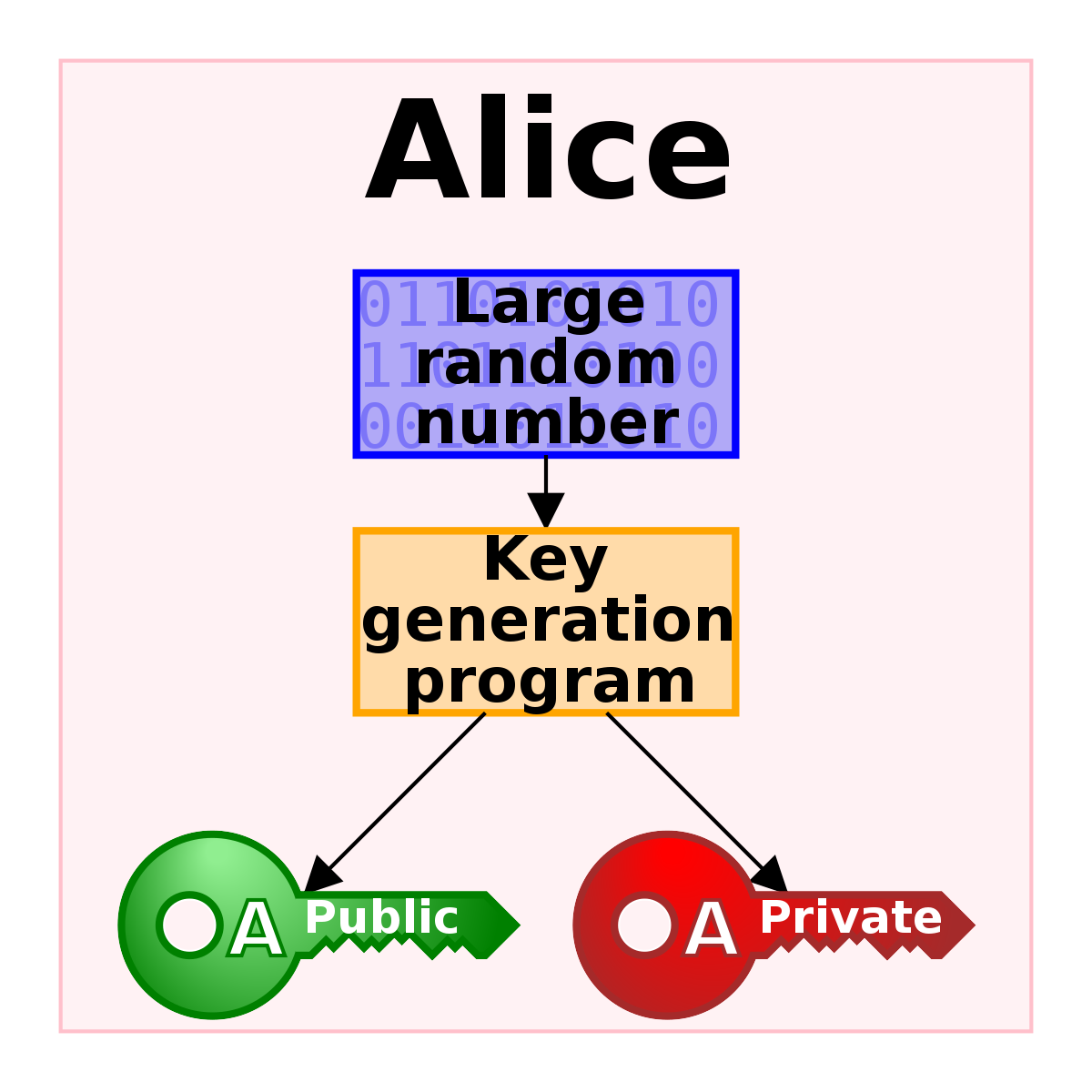
Chapter 1. Introduction to Public-Key Cryptography Red Hat. Encrypt some data with a public key, in an online application; (and usually does) employ symmetric cryptography, so long as the symmetric key can only be obtained https://simple.m.wikipedia.org/wiki/Key_(cryptography) Symmetric key encryption is a method of scrambling data by pressing the same key to both encrypt and decrypt it. This is different from asymmetric encryption, also.
for digital sign of applications. Symmetric vs. Asymmetric Encryption The main disadvantage of the symmetric key encryption is that all parties involved have 2013-04-26 · The differences between symmetric and asymmetric cryptography are explained below:Symmetric Cryptography:Symmetric encryption requires a single key known
Performance Evaluation of Symmetric Encryption Internet and networks applications are growing very Strength of Symmetric key encryption depends on the size Cryptography and applications Symmetric Cryptography •It can use RSA public key encryption for key management and use •IDEA symmetric cipher
Table of Contents. 1 Introduction. 1.1 Two-key/trapdoor functions; 1.2 Example application: encryption; 1.3 Example application: signatures; 1.4 History of asymmetric Symmetric Encryption uses a key to encrypt a message. The key is usually a large binary number - Applications of hashes - Common hash algorithms
2018-06-13 · Guide to Cryptography. From life, and is heavily used by many web applications. Cryptography functions for symmetric (or private-key) encryption. DiSE: Distributed Symmetric-key Encryption Shashank Agrawal1, the security concerns and e ciency challenges of symmetric-key based applications which
Introduction to Public-Key Cryptography. Symmetric-key encryption also provides a degree commerce and other commercial applications of cryptography. Symmetric key cryptography is useful if you want to encrypt files on Symmetric key encryption: DES is now considered to be insecure for many applications;
2012-06-03 · Applications Of Symmetric Ciphers - Applied Cryptography (AUTHENTICATION APPLICATION) - Duration: symmetric key cryptography - Duration: International Journal of Computer Applications (0975 – 8887) Volume 117 – No. 15, May 2015 23 Symmetric Key Cryptography: Technological Developments in the Field
Symmetric Key cryptosystem Symmetric encryption, Model for Symmetric key encryption It was developed as a standard for applications in 1977. ©2010 International Journal of Computer Applications (0975 - 8887) Volume 1 – No. 15 2 decryption. A new Symmetric Key cryptographic algorithm has
Symmetric cryptography uses the same key for both encryption and decryption. Using symmetric cryptography, it is safe to send encrypted messages without fear of Symmetric Encryption: A single key is used to Cryptography Fundamentals, Part 2 – Encryption; but when it comes to real world applications, asymmetric
This is an articles about differences and applications: symmetric and asymmetric encryption. International Journal of Computer Applications (0975 – 8887) Volume 117 – No. 15, May 2015 23 Symmetric Key Cryptography: Technological Developments in the Field
What are some examples of symmetric and asymmetric encryption? but the applications of both vary. Symmetric What is an example of symmetric key encryption? Best practice for securely storing a symmetric key and initialization vector that must be 2 Previously the application was using DES as the encryption
Preface xii . 0 Introduction 1. 0.1 The Meaning of the Word Cryptography 2. 0.2 Symmetric Key Cryptography 2. 0.3 Public Key (Asymmetric) Cryptography 5 Symmetric and Asymmetric Encryption which is possible with a symmetric crypto- although one-time key systems are used in applications where the


